Introducing Verifiable Compute.
Ready for Agentic AI.
Launching in 2025.
Evolve Trust for Agentic AI.
We’re introducing a new form of silicon-based trust for AI that allows users to verify at runtime the lineage and governance of any AI dataset, model, or agent.
With EQTY’s groundbreaking AI Notary System, persistent proofs of compliance in AI Certificates can be verified instantly or decades later without having to spend the time and money to rerun and reproduce complex AI workloads.



Lets You Verify:



91% of enterprises face software supply chain attacks each year.
This problem will grow exponentially as billions of autonomous AI agents are assembled and provisioned in the next 5 years.
You need new solutions to address new vulnerabilities distributed across your AI developers, partners, and suppliers.
Enforce Governance
Automate Auditing
Preserve Privacy
Verifiable Compute ensures your entire AI supply chain is secure, safe, and auditable.
Using a notary run in a trusted execution environment (TEE) on both the CPU and GPU, users can verify that an AI compute session is confidential and meets required governance controls before computation starts and continuously at runtime.
+80% Automate
Proof that AI deployments are untampered
Proof that AI models and data are confidential
Proof that AI guardrails are implemented
Proof that AI systems are performant
Proof that AI workloads stay in budget
Proof that AI processes are compliant
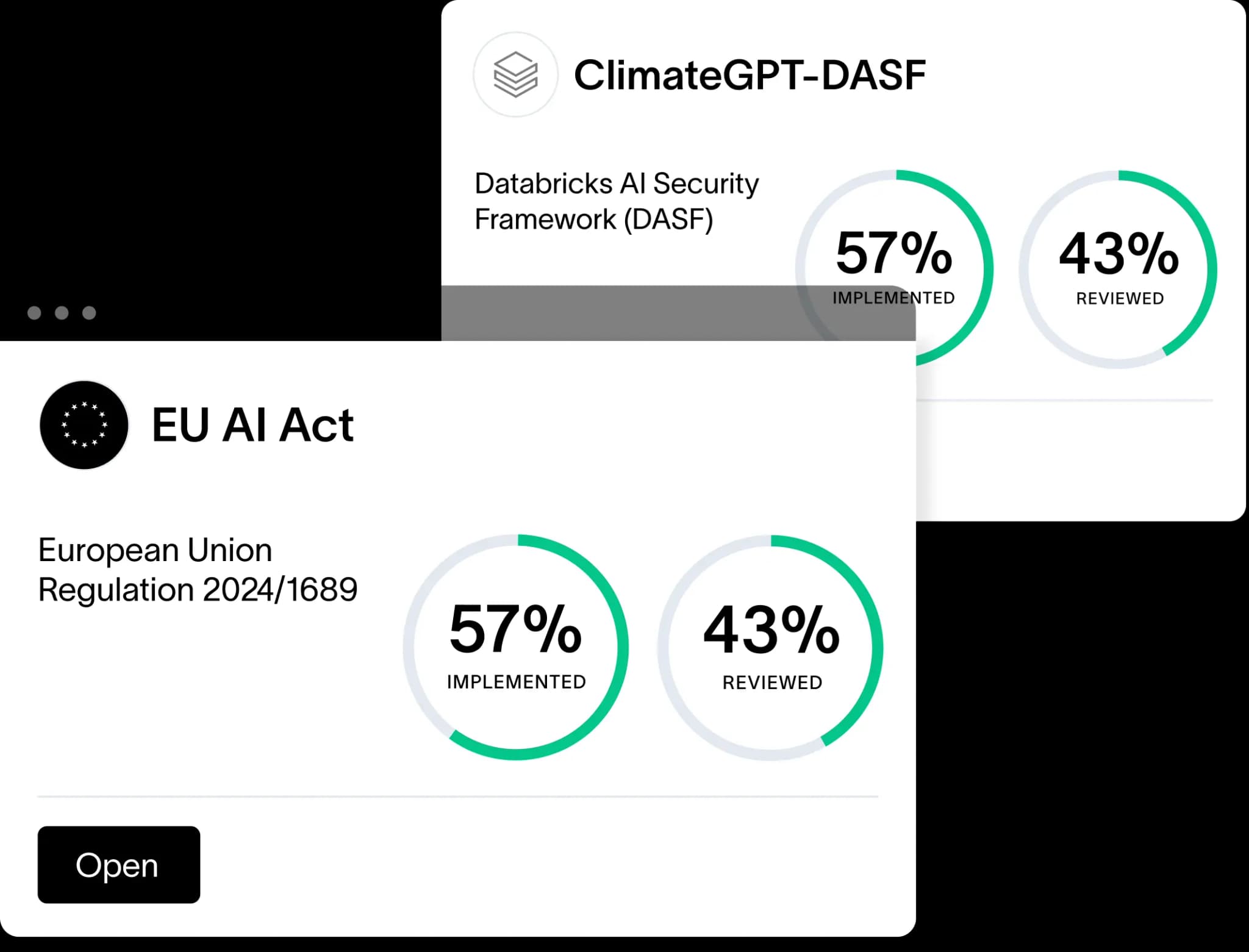
Get binding governance of your end-to-end software build pipeline.
Avoid IT vulnerabilities by reconfirming your software only includes components that have been approved for use. Provide visibility for all your stakeholders from DevSecOps, engineering, and product leaders.
Streamline compliance
Reduce supply chain risks
Integrate with CI/CD pipelines
Automate audits of all SBOM components

Auditable records of an agent`'s components and training.
Tamper-proof credentials that can be validated in any environment.
Authenticate what an agent is doing and control their dataflow and actions.

Align agent-to-agent interactions to policies at runtime.
На сколько прокрутить странице при скролле (пиксели)
Блокировка при последующей прокрутке (миллисекунды)



Learn about Node 1 in Reidsville, North Carolina
Population 14,566 and the World's First Verifiable AI

EQTY's Governance Studio is bundled with each Verifiable Compute node to tailor governance across all your stakeholder needs and automate over 80% of reporting requirements across your systems.
Prove the governance of your agentic workflow in real time.
Compliant
non-Compliant
inComplete
NA

From ChatGPT to Claude, verify the exact payload sent to closed source AI endpoints.
Verify exactly which embeddings were retrieved from a RAG database and used in inference.
Verify what data was used to fine tune an LLM, train a SLM, and prove it was accurately benchmarked.
Verify the model and its parameters were locally deployed at inference.

View a certificate of AI governance that is verified instantly in a browser.
Send certificates to partners and suppliers to extend and inherit trust in AI.
Audit AI manifests months, years, and decades later.

Verify AI app builds with a secure GitLab and GitHub runner
Witness 3rd party API calls to open and closed source models
Notarize any docker container to create verifiable runtime of AI models and agents
Develop with our SDK to verify granular AI system activity